Enterprise Browsers: The New Enterprise Security Platform
How enterprise browsers are reshaping identity, endpoint and network security
Enterprise browsers are fundamentally reshaping security by building essential protections directly into the browsing experience. Rather than bolting on various security tools, this approach makes security native to where work actually happens - in the browser itself. For organizations struggling with complex security stacks and poor user experience, enterprise browsers offer a compelling path to consolidation while strengthening security controls.
Why Now?
The rise of enterprise browsers stems from fundamental changes in how work happens and how to secure work. Three key trends are driving this transformation:
Remote work has rendered traditional perimeter security obsolete.
The proliferation of SaaS applications has created security challenges that legacy tools struggle to address.
Employee experience has become paramount, making traditional security approaches that create friction untenable.
Source: Emerging Tech: Security — The Future of Enterprise Browsers by Gartner
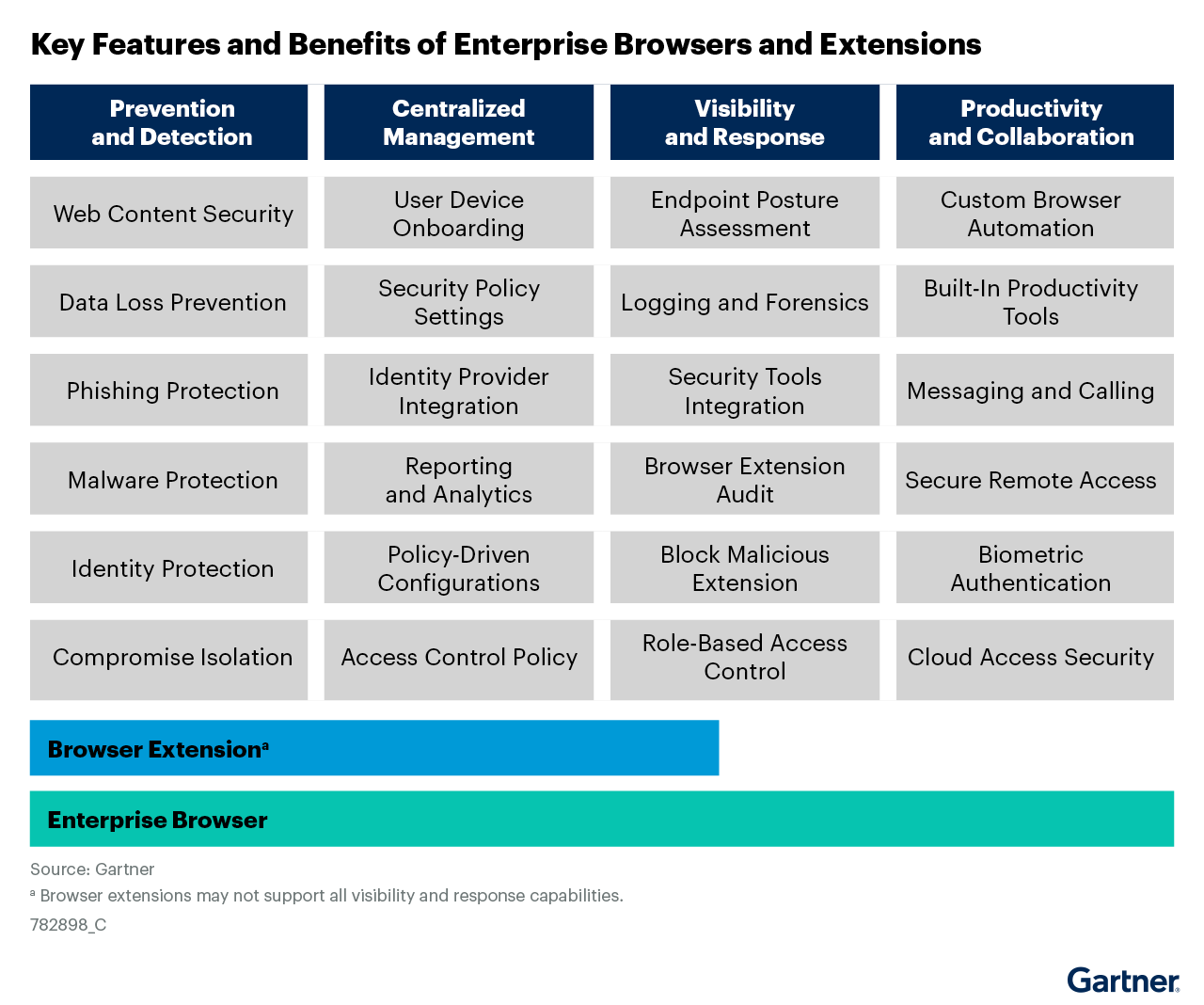
Core Product Features
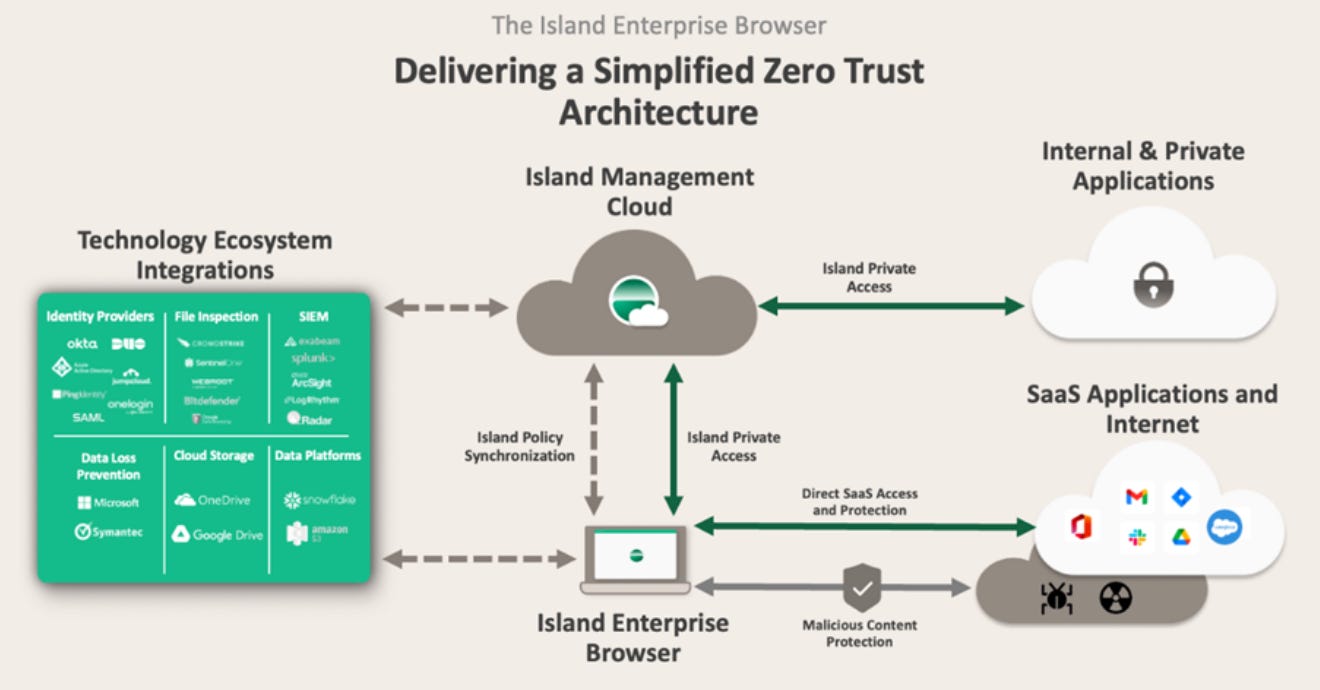
While enterprise browsers replace a lot of security tools, integrations with existing security providers still play a key role. CISOs integrate enterprise browsers with:
Core identity providers (e.g., Okta, Azure AD).
Endpoint protection platforms.
Network infrastructure security.
Key product features of enterprise browsers include:
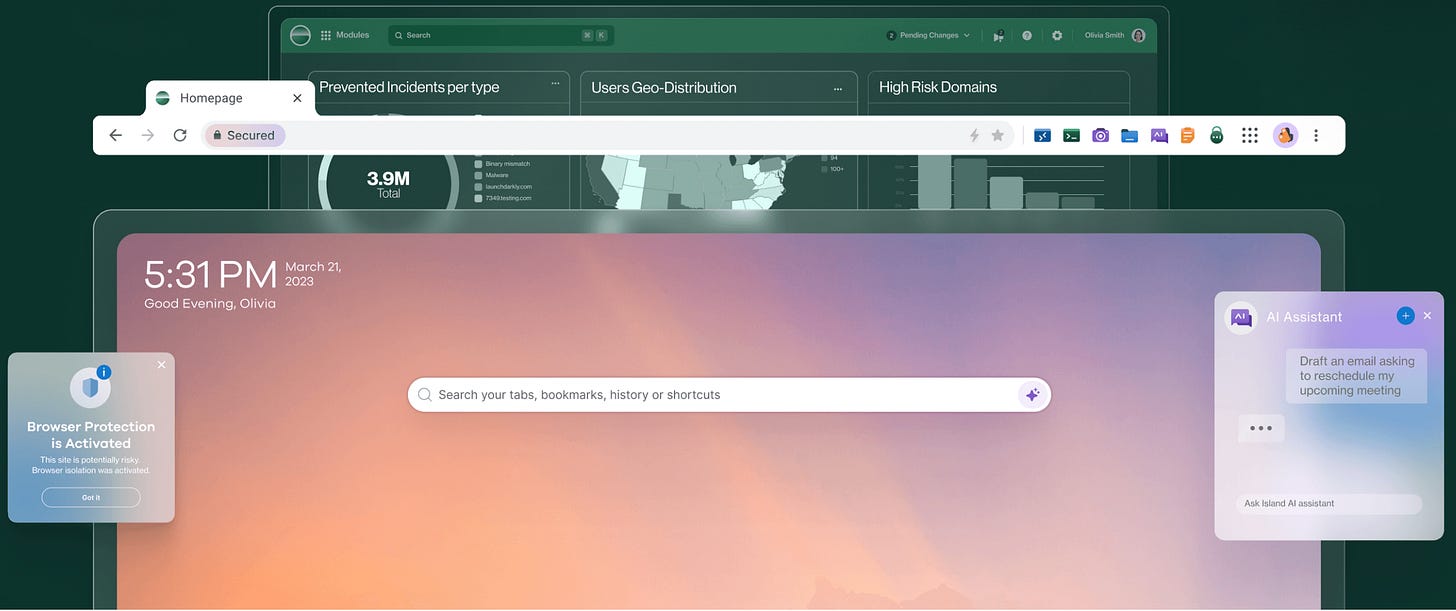
Identity Integration The browser naturally connects with your existing identity tools like Okta and Azure AD. This means seamless single sign-on, automatic policy inheritance, and stronger access controls without extra configuration.
Endpoint Protection Think of the browser as an always-on security agent. It detects malicious scripts, blocks keyloggers, and isolates dangerous content in real-time - all while checking that devices meet security requirements.
Network Security Instead of adding network security tools, the browser handles web traffic directly. This gives you complete visibility and control over all web activity, with built-in policy enforcement and filtering.
Anti-Phishing & Isolation The browser uses computer vision to detect fake logos and suspicious pages. For extra protection, it can render pages in disposable cloud containers, sending only safe content to users.
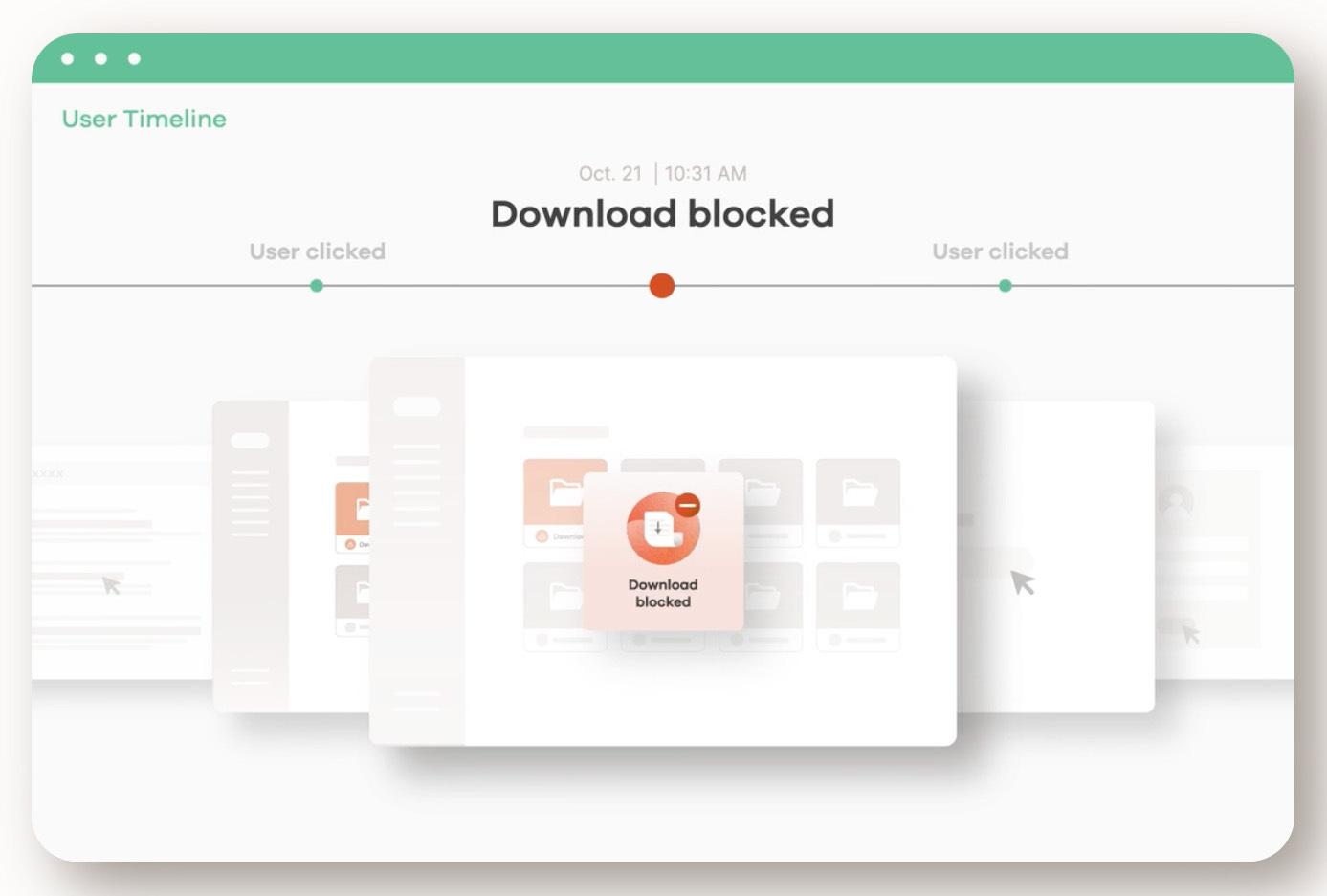
Data Protection Built-in controls prevent data leaks through downloads, screenshots, copy/paste, and more. The browser automatically watermarks documents and obscures sensitive information based on your policies.
Behavioral Monitoring The browser watches for suspicious patterns like unusual access locations, abnormal file activities, or shadow IT usage. This helps catch threats early while maintaining detailed audit trails.
Why CISOs love the Enterprise Browser?
CISOs love enterprise browsers because they consolidate multiple security tools into a single platform, simplifying operations and improving protection across diverse use cases. By integrating identity, endpoint, and network security, enterprise browsers reduce costs, minimize complexity, and enhance user experience without compromising security. This is a rare cost savings opportunity for CISOs.
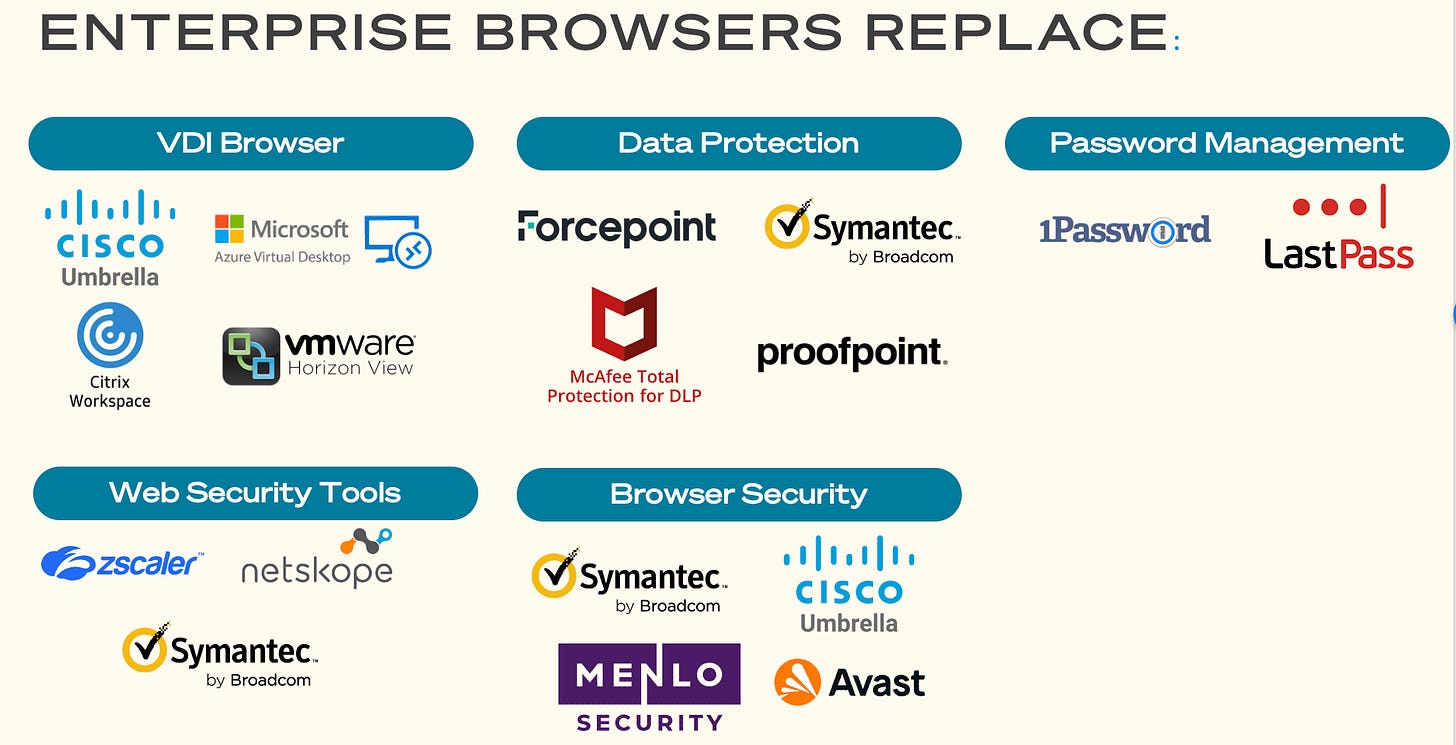
Here are core security tools that are often eliminated from implementing an enterprise browser:
1. Virtual Desktop Infrastructure (VDI)
Replaces: Citrix, VMware.
Benefit: Secure application access without high costs or performance penalties.
Ideal for: Contractor access and BYOD scenarios.
2. Web Security Tools
Replaces: Zscaler (secure gateway), Netskope (cloud security), Symantec Web Isolation
Benefit: Built-in functionality eliminates proxies and agents, providing better visibility and control.
3. Data Protection
Replaces: Forcepoint, McAfee DLP, Digital Guardian, Symantec DLP
Benefit: Seamless, granular data controls (e.g., file transfers, clipboard, screen captures) reduce friction while preventing leaks.
4. Browser Security
Replaces: Symantec Web Isolation, Cisco Umbrella, Menlo Security, Avast
Benefit: Integrated security eliminates the need for bolt-on solutions and improves performance.
5. Password Management
Reduces reliance on: LastPass, 1Password.
Benefit: Built-in zero-knowledge password architecture simplifies deployment and enhances security.
A CISO implementing Island noted:
"Island offered a lighter version of SASE without having to reroute data through the cloud." After experience with Zscaler, they found Island provided "better login and web gateway capabilities for employee experience," while delivering effective "data perimeter control."
Key Benefits of Enterprise Browsers:
Significant cost savings by eliminating multiple vendor contracts.
Improved security with unified policy management.
Enhanced user experience with fewer tools and agents.
Simplified IT management and reduced complexity.
Consistent protection across remote, cloud, and on-premise scenarios.
Competitive Landscape:
The enterprise browser market, led by players like Island, and Talon (Palo Alto Networks), is disrupting traditional web security by consolidating functionality into secure, Chromium-based platforms. These browsers compete with broader SASE and Zero Trust solutions (e.g., Zscaler, Netskope) and offer a lightweight alternative to costly VDI solutions like VMware and Citrix, making them a compelling choice for modern enterprise security needs.
Key players in the broader enterprise browser market include:
Island was the first mover in the enterprise browser space, focusing on creating a secure, enterprise-grade browsing environment. Built on Chromium, it combines familiarity with robust containerization technology that isolates browsing activities, preventing malware and data breaches. Island excels with its comprehensive security features, such as script blocking, encryption, and anomaly detection, and offers seamless deployment with minimal management overhead. Island’s strong enterprise GTM strategy and experienced founders have helped establish it as the most prominent player in the space.
Talon Cyber was founded in 2021 and quickly became a notable competitor in the enterprise browser market, leveraging its Chromium-based platform for endpoint security. Its technology supports corporate and personal devices, enabling monitoring, data loss prevention, and secure web gateway functionality. Talon also introduced a browser extension to extend security features to other browsers, enhancing flexibility for enterprises. With its acquisition by Palo Alto Networks for $625M, Talon is being integrated into Prisma SASE, solidifying Palo Alto’s position in delivering a more unified security platform.
Enterprise browsers overlap with Secure Access Service Edge (SASE) and zero-trust platforms such as Zscaler, Netskope, Cloudflare, and Palo Alto Networks (Prisma SASE). These vendors provide comprehensive security beyond the browser, addressing secure web gateways, identity, and SaaS protection. With Talon’s integration, Palo Alto strengthens its zero-trust capabilities, signaling increasing convergence between SASE and enterprise browser functionality. However, SASE vendors typically offer broader network security solutions, while enterprise browsers focus on the user-device interaction layer.
Microsoft Edge Enterprise, launched in 2023, focuses on separating personal and work browsing into isolated windows to prevent sensitive data leaks. While it benefits from Microsoft’s vast resources and partnerships, such as OpenAI’s Co-Pilot integration, it lacks the depth of features offered by native enterprise browser startups like Island and Talon. Microsoft’s bundling potential with its other products may attract SMBs, but its enterprise browser remains in an early stage compared to more mature competitors.
Google Chrome Enterprise, introduced in 2017, has recently enhanced its secure browser features, including integrations with BeyondCorp Enterprise for zero-trust web security. It offers robust malware and phishing protection for both managed and unmanaged devices. However, despite Google’s scale, its enterprise browser features are less developed compared to startups like Island, particularly in integrations with security tools such as SSE and EDR vendors. While Google is making strides, it is still catching up to market leaders.
VDI Browsers are legacy solutions like VMware Horizon View, Citrix Workspace, and Microsoft Azure Virtual Desktop and are losing ground to enterprise browsers. While VDI provides strong isolation and secure access, it is expensive and complex to deploy compared to modern enterprise browsers. Enterprise browsers such as Island and Surf offer lightweight, cost-effective alternatives, particularly for BYOD and contractor use cases, providing comparable security without the management overhead of traditional VDI.
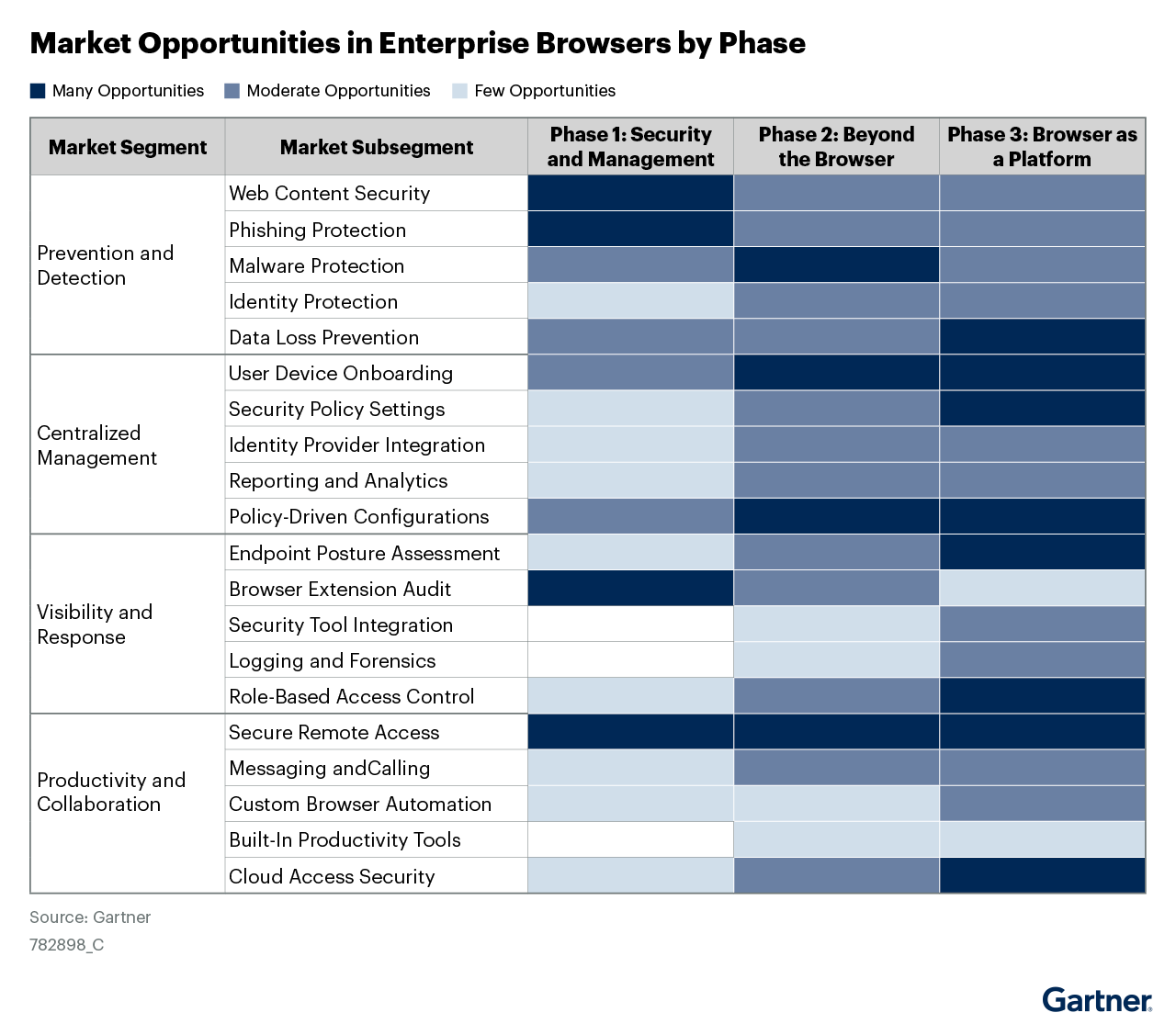
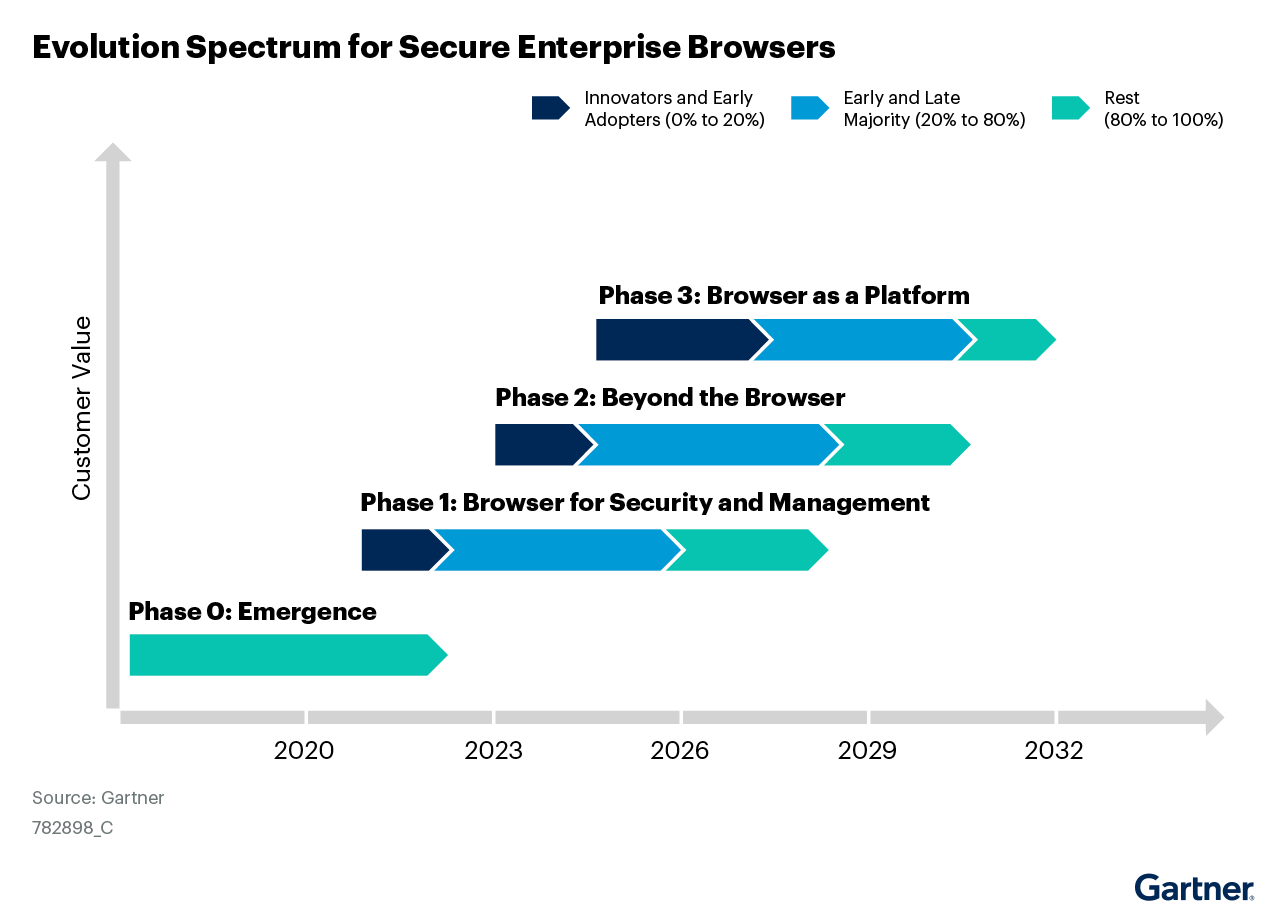
Market Trajectory
Gartner's forecasts indicate rapid adoption:
By 2025: Enterprise browsers in 25% of web security decisions (up from 5%)
By 2026: 25% of enterprises using managed browsers (up from 10%)
By 2027: Central to enterprise superapp strategies
By 2030: Core platform for workforce productivity and security
According to Gartner's projections, this is just the beginning of a major transformation in enterprise security.
Source: Emerging Tech: Security — The Future of Enterprise Browsers by Gartner
Conclusion
While consumer browsers have seen dramatic innovation since Netscape's launch in 1998 and Chrome's arrival in 2008, enterprise browsers represent an untapped opportunity for reimagining how work gets done. The monthly performance updates and AI wars between Microsoft and Google have primarily focused on consumer use cases, leaving a gap in browsers purpose-built for enterprise security and productivity.
The enterprise browser approach recognizes that organizations need more than just a consumer browser with security bolted on - they need a complete platform that consolidates security, compliance, and productivity tools into the primary workspace where employees spend their day. This shift from fragmented tools to a browser-centric enterprise platform promises to both reduce costs and strengthen security by making the browser itself the foundation of the enterprise work environment.




Really helpful! Wondering how these interact with internal, data-level, role-based access controls.
Thanks!
Great summary about the enterprise browser market. Our customers are seeing the benefit of moving security from networking layer to endpoints, with greater control and enhanced security. The vendor list misses Mammoth Cyber though.